IdS ServiceManager - HELHETLIG PLATTFORM FOR IAM, IGA OG GRC
Kontroll, sikkerhet og etterlevelse i én løsning
- Styr identiteter og tilganger (IAM)
- Sikre styring og etterlevelse (IGA/GRC)
- Automatiser prosesser for effektiv virksomhetsstyring
Tiltrodd av
Fra kaos til full kontroll
Alltid bestå revisjoner. Enkelt.
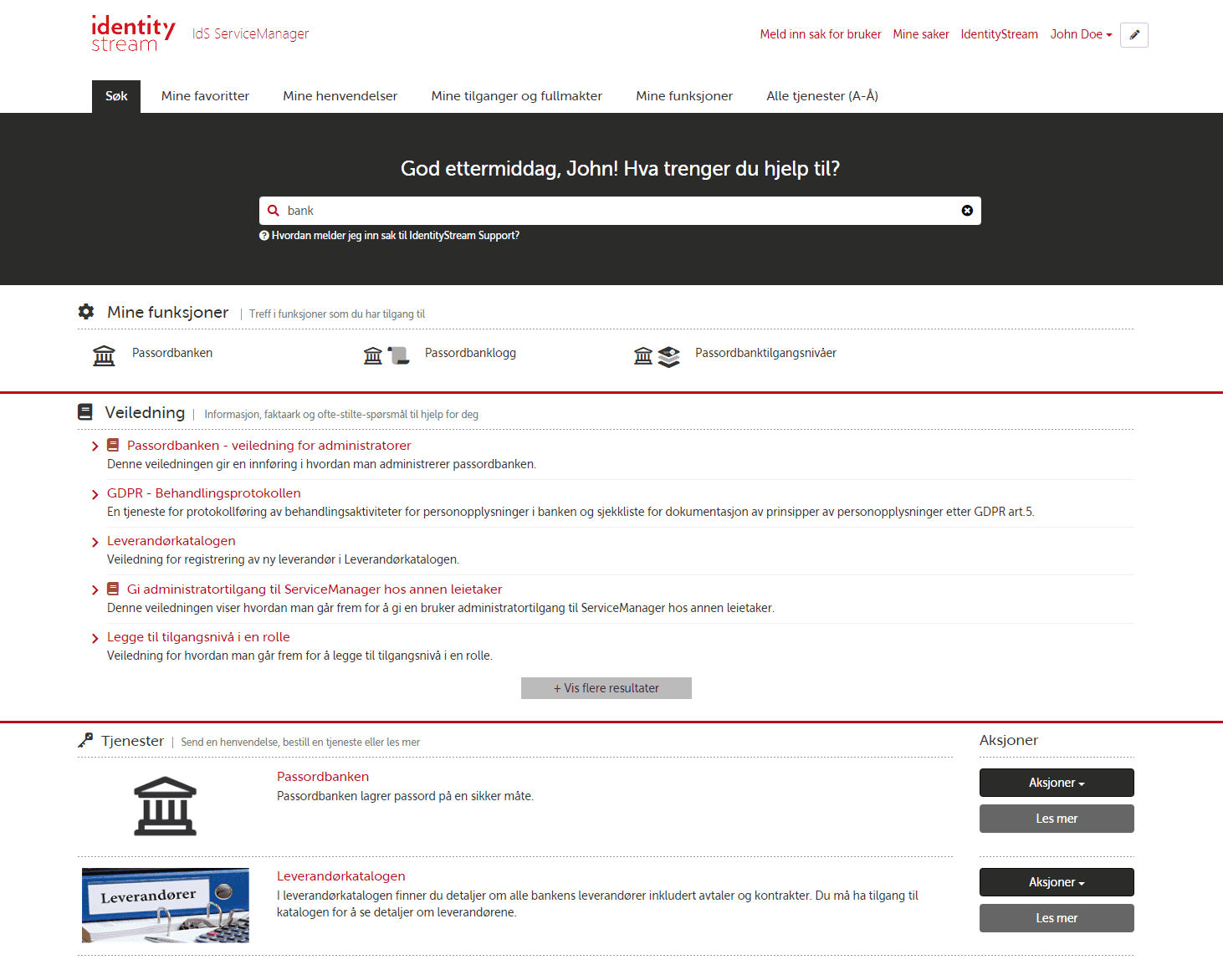
I samsvar
- Oppfyll krav fra tilsynsmyndigheter og revisor - full støtte for bank & finans og andre regulerte bransjer.
Samlet
- Samle IGA, GRC og kontraktsadministrasjon i én løsning.
Automatisert
- Sikre sømløs og automatisert dataflyt mellom systemer.
Verifisert
- Beskytt kritiske prosesser med fire-øyne-prinsippet.
Identitetssikkerhet
Rett tilgang, til rett person, til rett tid
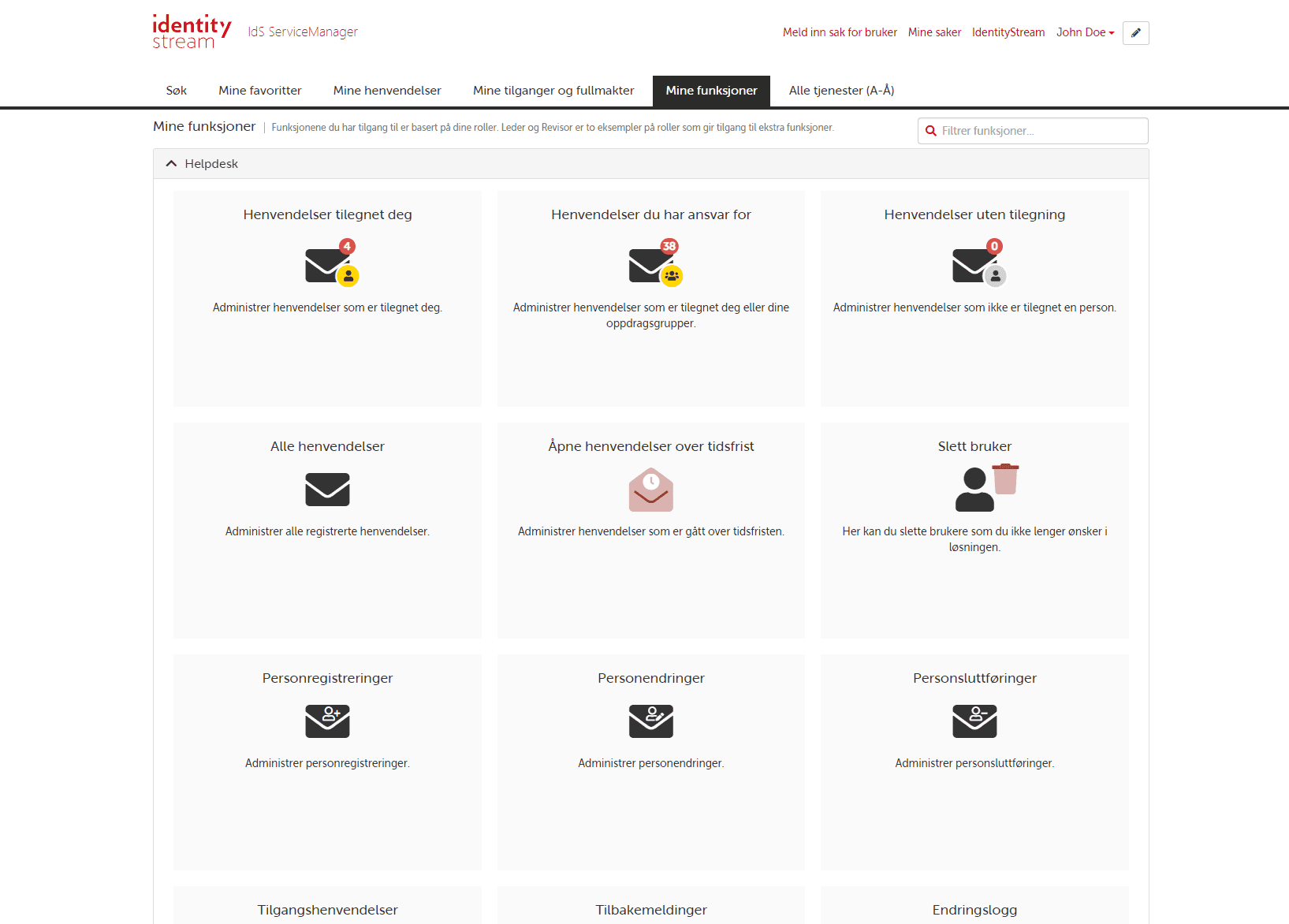
Sikkert
- Gi rett tilgang, til rett person, til rett tid. Minimer risiko for menneskelig feil.
Konsistent
- Følg hver ansatt gjennom hele karrieren med automatiserte regler basert på roller og avdeling.
Enkelt
- Forenkler og forbedrer arbeidshverdagen til brukerstøtte.
Integrert
- Sømløst integrert med de systemene du bruker hver dag.
Komplementære moduler
Gjør sikkerhet til et konkurransefortrinn
Identity & Access Management (IAM)
Identitets- og tilgangsstyring med 80% av norske sparebanker på kundelisten.
Les merIdS SignatureManager
Effektiviser og standardiser bruk av epostsignaturer i bedriften din med IdS SignatureManager.
Les merContractManager
Administrering av kontrakter med automatiserte påminnelser som sparer deg for tid og penger.
Les merPassordbanken
Gi ansatte, hele avdelinger eller team sitt eget passordhvelv. Med multi-faktor autentisering.
Les merRegTech
Regulatoriske tjenester og prosesser.
ITSM
IT Service Management med kunnskapsdatabase for ofte-stilte-spørsmål.
HR
Inneholder blant annet funksjoner for rekruttering og signering av etiske retningslinjer.
Risk
Lar fremoverlente foretak ta riktig risiko.
Tjenester og rådgivning
Digitalisering gjort enklere, smartere og tryggere

Microsoft 365 & SharePoint
Utnytt mulighetene som finnes i SharePoint, Teams og digital samhandling.
Med vår erfaring og innsikt får du custom webparts, skreddersydde integrasjoner og trygg tilgangsstyring som fører til økt brukeradopsjon og en bedre arbeidshverdag.

Microsoft Azure
Over 95% av Fortune 500-virksomheter bruker Azure i sine digitaliseringsinitativ.
Vi kan rådgi og komme med anbefalinger innenfor oppsett av brukerstyring, applikasjonsutvikling og tjenester som jobber i bakgrunnen.

Applikasjonsutvikling
La oss løse dine programmeringsbehov.
I tillegg til å levere vår egen software, ServiceManager, lager vi skreddersydde og frittstående løsninger – både for sky og on-premise.
Referanser
De beste folkene
Møt teamet
Ta kontakt
- Adresse
IdentityStream AS
Laberget 22
4020 Stavanger
- Telefonnummer
- (+47) 908 94 895
- E-post
- hello@identitystream.com

















